Preliminaries
- Image via Wikipedia
1. Before you start metaphor hacking you must first accept that you don’t have a choice but to speak in some sort of a figurative fashion. Almost nothing worth saying is entirely literal and there are many things whose “literalness” is rooted in metaphor. Look at “I sat in a chair the whole day.” Looks very literal at first glance but it depends on our understanding of a chair as a container (e.g. he was spilling out of his chair) and the day as an object (e.g. she was counting the days, cutting the day short, a long day, etc.)
2. You must also learn to recognize how metaphors are constructed through mappings from one domain to another. Sometimes these mappings are explicit, sometimes they are hidden, sometimes they are clear cut one-on-one connections and sometimes they are fuzzy and cross levels of categorization. But they’re there. If you say, “life is a journey” you can also say “I’ve reached a fork in the road” or “I’ve hit a rough patch” because you map elements of the “road/journey domain” such as intersections, rocky surfaces, hills, etc. to elements of the “life domain” such as decisions and difficult time periods. This way of thinking about metaphor was popularized by Lakoff and Johnson in their 1980 book “Metaphors we live by” which is a great weekend read. However, do read the 2003 edition which contains an important additional chapter.
Metaphor hacking
Once you’ve done the above, you can start hacking (or really do them at the same time).
1. Find an example of a metaphor being used in a way that limits your ability to achieve something or one that constrains your thinking or actions. For example, “education is a marketplace.”
2. Identify the domains involved in the metaphor. The source domain is the domain of knowledge or experience which is being used to structure our understanding of the target domain. This is frequently being confused with concrete/abstract or known/unknown but very often the source domain is just as abstract or well/little known as the target domain. For example: The source domain of marketplace and business is no more concrete or better known than the target domain of education. But it can still be used to structure our understanding of the domain education.
3. Identity the most common mappings between the source and target domains. These generally have the form of “X is (like) Y” and carry with them the assumption that if X is like Y, it should have a similar relationship to Z or perform similar activities. The “is like” function relies on a fuzzy concept of identity, a sort of family resemblance. For example, in the “education is a marketplace” metaphor, some common mappings are “students are customers” and “schools are companies providing a service”. Don’t make any judgements at this stage. Simply list as many mappings as you can find.
4. See which of the existing mappings are problematic in some way. Some mappings may lead us to others which we didn’t set out to create. This could be good or bad. For instance, if we think of students as the clients of schools, it’s a very short step to thinking of teachers as service staff and performance pay. This may be good or bad. But it also leads to students saying “I’ve paid you money for my education” so I deserve to pass. Which is a consequence very few would describe as good. You can also find some one-to-many mappings to see where the metaphor may get you into trouble. For example, if schools are businesses who is their customer? Students, parents, government or society? What is the currency? Knowledge, career prospects, etc. There’s nothing intrinsically wrong with one-to-many mappings but they can underscore a possible problem area in the way the metaphor is being used to generate new understandings.
5. Finally, find other possible mappings and try to imagine what the consequences would be. For this, you must strive to learn as much as possible about both of the domains involved and keep an open mind about the mappings. Anything goes. This can be done in a negative manner to bring into question the premise of the metaphor. For instance, Jeffrey Henig pointed out in his book on the Market Metaphor in education that one of the key prerequisites to the functioning of the market is a failure of business entities but none of the market reformers in education have provided a sufficient alternative to failure in their market model of schools. This should certainly give the market advocates a pause. It doesn’t automatically mean that the marketplace metaphor cannot help us understand education in a useful way but it points to a possible limit to its utility. This process is similar to the rhetorical technique known as reductio ad absurdum but it has a different purpose. Also the metaphor hacker will approach this process with an open mind and will rule nothing out as a priori absurd but will also understand that all these mappings as just options not necessary consequences.
But driving a metaphor forward is most often a positive experience. Donald A Schön called this kind of metaphor use the “generative metaphor”. He gives a great example from engineering. When trying to design a new type of synthetic bristle for a paintbrush, a group of engineers was stuck because they were trying to figure out how to make the paint stick to the threads. This led to blobs of paint rather than nice smooth surfaces. Until one engineer said “You know what, a paintbrush is really a pump”. And immediately the research shifted from the surface of the bristles to their flexibility to create a pump like environment between the bristles rather than trying to make the paint stick to them. Anywhere else the “paintbrush is a pump” metaphor would have seemed ridiculous but in this context it didn’t even need an explanation. The engineers just got on with their work.
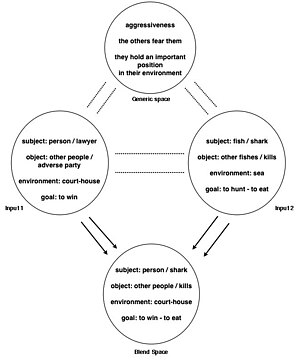
This process never stops. You can always find alternative mappings or alternative domains to help you understand the world. You can even have more than one source domain in a process called blending (or conceptual integration) that generates new domains Fauconnier and Turner give the example of a computer virus which blended the domain of software with the domain of medicine to generate a domain of computer viruses that has some properties of both and some emergent properties of its own. But this is for another time.
Conclusion
All good hackers, engineers, journalists or even just members of a school or pub debate club have been hacking at metaphors ever since the phrase “is like” appeared in human language (and possibly even before). But this post urges a transition from hacking at metaphors to hacking metaphors in the best sense of the word. This requires some work at understanding how metaphors work and also getting rid of quite a few prejudices. We’re all used to dismissing others’ arguments as just metaphors and “literalness” is seen as virtue. Once we accept metaphors for what they are, we can start using them to improve how we think and what we do. Not through a wholesale transformation but through little tweaks and a bit of conceptual duct tape. And that’s what the hacker spirit is all about.
Readings
- George Lakoff and Mark Johnson, Metaphors we live by (Chicago: University of Chicago Press, 1980).
- Jeffrey R. Henig, Rethinking school choice: limits of the market metaphor (Princeton, N.J.: Princeton University Press, 1994).
- Donald Alan Schön, Displacement of concepts (London: Tavistock Publications, 1963).
- Donald A. Schön, “Generative metaphor: A perspective on problem-setting in social policy,” in Metaphor (Cambridge: Cambridge University Press, 1979), 254-283.
- Gilles Fauconnier and Mark Turner, The way we think: conceptual blending and the mind’s hidden complexities (New York: Basic Books, 2002).
